Site Security Report
In today's digital landscape, securing your website with an SSL (Secure Sockets Layer) certificate is more important than ever. Not only does SSL protect sensitive information exchanged between users and your site, but it also enhances your site's credibility and boosts its search engine ranking. This guide will walk you through the process of installing SSL, discuss the common errors you might encounter, and provide troubleshooting tips to ensure your website remains secure and trustworthy.
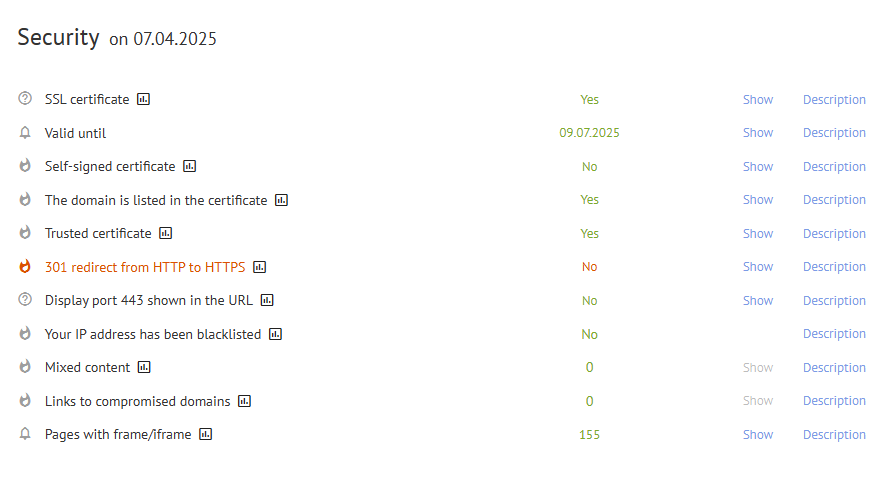
By clicking on the "Description" link, you will find tooltips with detailed information about these parameters, explaining their significance for your website's security.
In this article, we will delve into several key elements of your site's security report, starting with the SSL certificate.
Understanding SSL Certificates
SSL certificates are a critical component of online security. They establish an encrypted connection between a web server and a browser, ensuring that all data transferred between them remains private and secure. When a user connects to a website with SSL, they will see a padlock icon in the address bar, indicating that their connection is secure. Additionally, Google has begun to use HTTPS as a ranking signal, meaning that websites utilizing SSL can enjoy improved visibility in search engine results.
There are various types of SSL certificates available, including single-domain, multi-domain, and wildcard certificates. Each type serves different purposes and is suited for different website structures. Understanding the differences can help you choose the right certificate for your needs.
Types of SSL Certificates
- Single-Domain SSL Certificates: These certificates secure one specific domain. They are ideal for small businesses or personal websites.
- Multi-Domain SSL Certificates: These certificates can secure multiple domains and are perfect for businesses that manage several websites.
- Wildcard SSL Certificates: Wildcard certificates secure a single domain and all its subdomains, making them a cost-effective option for larger organizations.
- Extended Validation (EV) SSL Certificates: These certificates provide the highest level of validation and display the organization's name in the browser's address bar, enhancing user trust.
Why You Need an SSL Certificate
There are several compelling reasons to install an SSL certificate on your website:
- Data Protection: SSL encrypts sensitive information such as credit card details, login credentials, and personal data, protecting it from eavesdroppers and hackers.
- Improved SEO: Google prioritizes secure websites in its search rankings, meaning that having SSL can improve your visibility and attract more visitors.
- User Trust: The padlock icon in the browser's address bar signals to users that your website is secure, increasing their confidence in your brand.
- Compliance: Many regulatory frameworks require data protection measures, and having SSL can help you comply with these regulations.
How to Install SSL Certificates
Installing an SSL certificate involves several steps, which may vary depending on your hosting provider and server type. Below are general instructions to guide you through the installation process:
Step 1: Choose Your SSL Certificate
Begin by selecting the appropriate SSL certificate for your website. Consider factors such as the number of domains you need to secure and the level of validation required. Once you've made your choice, purchase the certificate from a trusted Certificate Authority (CA).
Step 2: Generate a Certificate Signing Request (CSR)
A CSR is a block of encoded text that contains information about your domain and organization. To generate a CSR, follow these steps:
- Log in to your web hosting control panel (e.g., cPanel, Plesk).
- Navigate to the SSL/TLS section.
- Select "Generate a CSR" and fill in the required details, including your domain name, organization name, and contact information.
- Submit the form to generate the CSR. Copy the CSR code as you will need to provide it to your Certificate Authority.
Step 3: Submit the CSR to Your Certificate Authority
After generating the CSR, you'll need to submit it to your chosen Certificate Authority. This process may involve additional validation steps, depending on the type of certificate you are purchasing:
- Domain Validation (DV): You will typically receive an email to verify ownership of the domain.
- Organization Validation (OV): This requires additional documentation to verify your organization’s details.
- Extended Validation (EV): This involves a rigorous vetting process and may take longer to complete.
Step 4: Install the SSL Certificate
Once your SSL certificate is issued, you will receive an email containing your certificate files. Here’s how to install it:
- Log in to your web hosting control panel.
- Navigate to the SSL/TLS section.
- Select "Manage SSL Sites" or a similar option.
- Upload the certificate files provided by your Certificate Authority, which typically include the server certificate, intermediate certificate, and root certificate.
- Save your changes and ensure that the SSL certificate is active.
Step 5: Configure Your Website to Use HTTPS
After installing your SSL certificate, you need to configure your website to use HTTPS instead of HTTP. Here are some steps to do this:
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
- Update your website’s configuration files. For Apache servers, you can do this by editing the .htaccess file to force HTTPS connections. Add the following lines:
- Update internal links throughout your website to point to the HTTPS version instead of HTTP.
- Set up a 301 redirect from HTTP to HTTPS to ensure users and search engines are redirected to the secure version of your site.
Step 6: Test Your SSL Installation
To ensure that your SSL certificate is functioning correctly, use online tools such as SSL Labs' SSL Test. This tool will analyze your SSL configuration and report any issues. You can also check for:
- Correct installation of the certificate chain.
- SSL/TLS version support.
- Vulnerabilities or misconfigurations in your SSL setup.
Best Practices for SSL Management
Maintaining a secure environment and ensuring the effectiveness of your SSL certificates requires ongoing diligence. Here are some best practices to follow:
Header set Strict-Transport-Security "max-age=31536000; includeSubDomains"
- Regularly Update Your Certificates: Keep track of expiration dates and renew your SSL certificates in a timely manner to avoid lapses in security. Set reminders for renewal at least a month in advance.
- Use Strong Encryption: Ensure that your SSL configuration uses strong encryption protocols (like TLS 1.2 or higher) to protect data in transit. Regularly review and update your server's cipher suites to disable any outdated or insecure protocols.
- Implement HSTS: Use HTTP Strict Transport Security (HSTS) to enforce secure connections and prevent downgrade attacks. This can be done by adding the following line to your .htaccess file:
- Monitor Your Site: Regularly check your website for SSL vulnerabilities and misconfigurations using online tools and security scanners. This proactive approach can help identify issues before they become significant problems.
- Educate Your Team: Ensure that everyone involved in managing your website understands the importance of SSL and security best practices. Regular training sessions can help maintain awareness of security protocols.
Common SSL Errors and Troubleshooting
Even after successfully installing an SSL certificate, you may encounter common errors that can affect your website’s security and performance. Here are some of the most frequent issues and their solutions:
- Mixed Content Issues: This occurs when a webpage served over HTTPS contains links to resources (like images, scripts, or stylesheets) that are served over HTTP. To resolve this, ensure that all resources are loaded over HTTPS. You can use browser developer tools to identify mixed content warnings and update the links accordingly.
- Certificate Trust Problems: If users receive warnings that your certificate is not trusted, it could be due to an incomplete certificate chain. Ensure that you have installed all required intermediate certificates provided by your Certificate Authority. These certificates help browsers recognize your SSL certificate as valid.
- Domain Mismatch: This error occurs when the domain name in the SSL certificate does not match the domain name in the URL. To fix this, ensure that the SSL certificate is issued for the correct domain. If necessary, you may need to reissue the certificate with the appropriate domain name.
- Expired Certificates: An expired SSL certificate will trigger browser warnings and can lead to loss of trust from users. Regularly monitor your certificate’s expiration date and set reminders for renewal. Some hosting providers offer automatic renewal options to simplify this process.
- SSL Configuration Errors: Misconfigurations can lead to various issues, including SSL handshake failures. Use tools like SSL Labs' SSL Test to analyze your SSL configuration and identify any errors. Follow the recommended fixes to ensure your server is configured correctly.
Maintaining SSL Security
Once your SSL certificate is installed and functioning correctly, maintaining its security is crucial. Here are some strategies to keep your SSL environment secure:
- Regular Security Audits: Conduct periodic security audits to assess the overall security posture of your website. This includes checking for vulnerabilities, outdated software, and compliance with security best practices.
- Update Software Regularly: Ensure that your web server, CMS, and any plugins or extensions are up to date. Software updates often include security patches that protect against known vulnerabilities.
- Implement Security Headers: Enhance your website's security by adding HTTP headers such as X-Content-Type-Options, X-Frame-Options, and Content-Security-Policy. These headers help mitigate various types of attacks, including cross-site scripting (XSS) and clickjacking.
- Backup Your Website: Regularly back up your website and database. In the event of a security breach or data loss, having recent backups can expedite recovery and minimize downtime.
- Use a Web Application Firewall (WAF): A WAF can help protect your website from various threats, including DDoS attacks, SQL injection, and other common vulnerabilities. Consider using a reputable WAF service to enhance your website's security.
Consulting with SSL Experts
If you are unsure about any aspect of SSL installation or management, consider consulting with SSL experts or utilizing resources from reputable SSL providers. Many Certificate Authorities offer support services to help you navigate the complexities of SSL management. They can provide guidance on certificate selection, installation, and best practices for maintaining a secure environment.
Additionally, many hosting providers offer SSL installation services as part of their packages. If you are not comfortable handling the installation yourself, reaching out to your hosting provider can save you time and ensure that your SSL certificate is set up correctly.
Conclusion
In conclusion, securing your website with an SSL certificate is essential for protecting user data, enhancing your site’s credibility, and improving search engine rankings. By following the steps outlined in this guide, you can successfully install and manage your SSL certificate, ensuring a secure environment for your visitors.
Remember to stay vigilant by regularly updating your certificates, monitoring your site for vulnerabilities, and adhering to best practices for SSL management. With ongoing diligence, you can maintain a secure website that instills trust in your users and effectively safeguards their sensitive information.
For further assistance, don't hesitate to reach out to SSL experts or explore resources from reputable SSL providers. By prioritizing SSL security, you are taking a significant step towards building a safer online presence for your business and its customers.
